Israeli 'Predator' Smartphone Spyware Exposed
All my investigations are free to read, thanks to the enormous generosity of my readers. Independent journalism nonetheless requires investment, so if you value this article or any others, please consider sharing, or even becoming a paid subscriber. Your support is always gratefully received, and will never be forgotten. To buy me a coffee or two, please click this link.
New research published by Amnesty International exposes the disturbing internal workings of Intellexa, and its constellation of digital espionage products. This includes ‘Predator’, a highly invasive resource linked to grave human rights abuses in multiple countries. Intellexa’s menacing technology allows government customers to access target smartphones’ cameras, microphones, encrypted chat apps, emails, GPS locations, photos, files, browsing activity, and more. It’s just the latest example of an Israeli-linked spyware specialist acting with no consideration for the law - although one wouldn’t know that from Amnesty’s probe.
Intellexa is among the world’s most notorious “mercenary spyware” purveyors. In 2023, the company was fined by Greece’s Data Protection Authority for failing to comply with its investigations into the company. An ongoing court case in Athens implicates Intellexa apparatchiks and local intelligence services in hacking the phones of government ministers, senior military officers, judges and journalists. Oddly unmentioned by Amnesty International, Intellexa was founded by Tal Dilian, a senior former Israeli military intelligence operative, and is staffed by Zionist entity spying veterans.
In March 2024, following years of damaging disclosures about Intellexa’s criminal activities, the US Treasury imposed sweeping sanctions on Dilian, his closest company confederates, and five separate commercial entities associated with Intellexa. Yet, these harsh measures were no deterrent to Intellexa’s operations. The company’s service offering has only evolved over time, becoming ever-more difficult to detect, and increasingly effective at infecting target devices. Typically, civil society and human rights activists, and journalists, are in the firing line.
On December 3rd, Google announced Intellexa’s targets numbered at least “several hundred”, with individuals based in Angola, Egypt, Kazakhstan, Pakistan, Saudi Arabia, Tajikistan, Uzbekistan and elsewhere potentially affected. Predator frequently relies on “one-click” attacks to infect a device. Users open a malicious link, which installs spyware that breaks open their chats on Signal, Telegram, WhatsApp and other platforms, audio recordings, emails, device locations, screenshots and camera photos, stored passwords, contacts and call logs, and the device’s microphone.
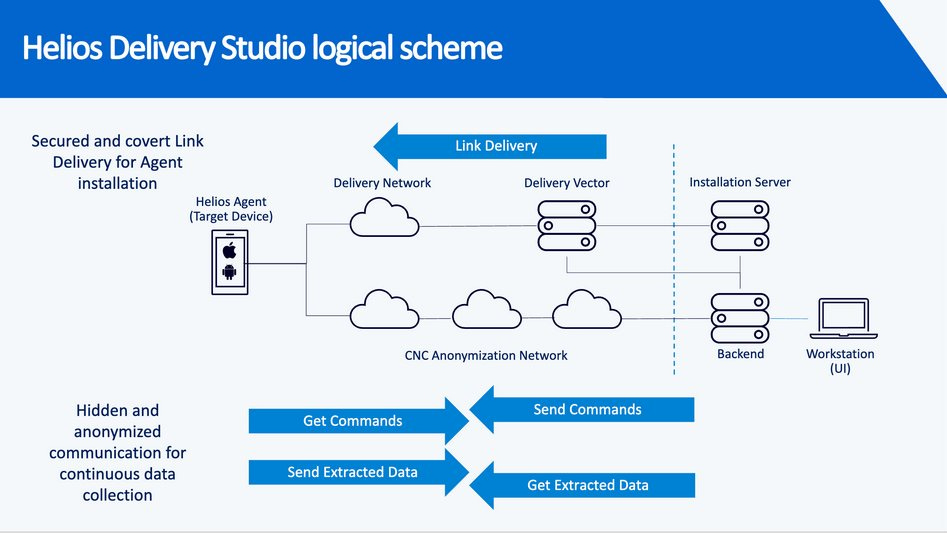
The vast data trove then passes through a chain of anonymising servers to hide its end destination, before being received by a customer. Predator also boasts a number of unique features designed to obscure its installation on a device from targets. For example, the spy tool assesses a device’s battery level, and whether it’s connected to the internet via sim card data or WiFi. This allows for a bespoke extraction process, ensuring devices aren’t obviously drained of network or power, to avoid stoking user suspicion.
Aladdin’s Cave
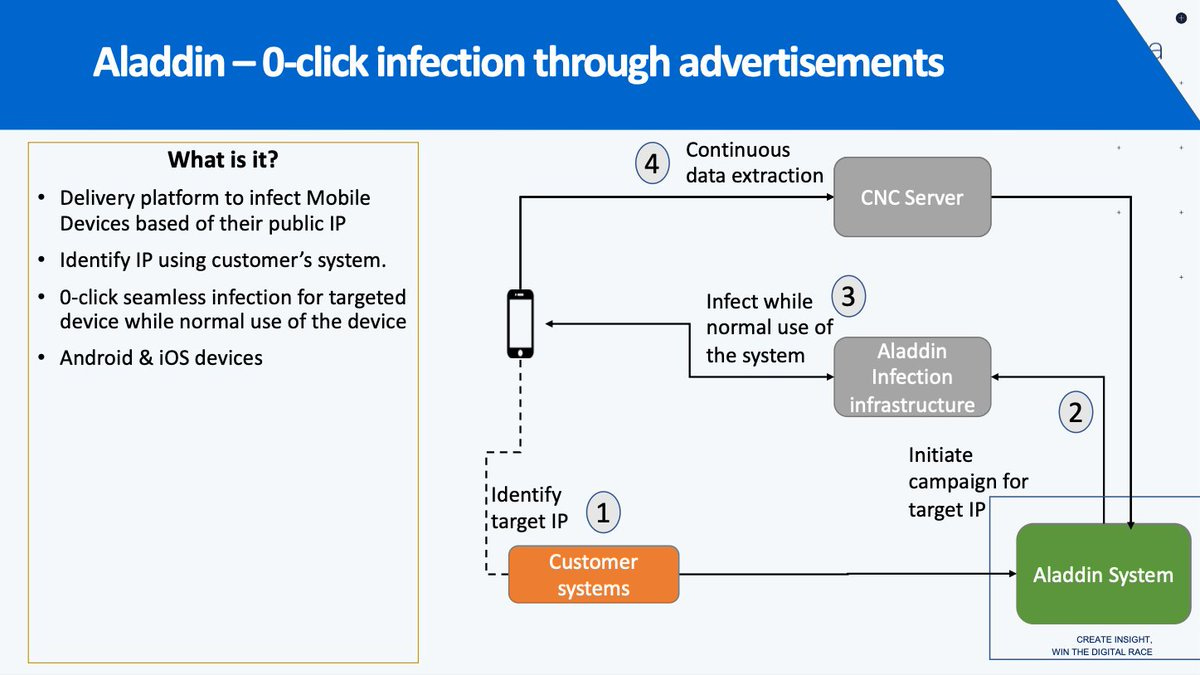
If Predator senses it has been detected, the spyware will even “self-destruct” to leave no trace of its presence on an impacted device. The methods by which Intellexa installs its malign tech on target devices is just as ingenious, and insidious. On top of “one-click” attacks, Intellexa is a pioneer in the field of “zero-click” infiltration. Its resource ‘Aladdin’ exploits internet advertising ecosystems, so users need only view an ad - without interacting with it - for spyware to infect a device.
Such ads can appear on trusted websites or apps, resembling any other advert a user would normally see. This approach requires Intellexa to pin down a “unique identifier” - such as a user’s email address, geographical location, or IP - to accurately serve them a malicious advert. Intellexa’s government customers can often readily access this information, simplifying accurate targeting. Research published by Recorded Future indicates Intellexa has covertly established dedicated mobile ad companies to create “bait advertisements”, including job listings, to lure in targets.
Aladdin has been under development since 2022 at least, and grown considerably more sophisticated since. Troublingly, Intellexa is not the only company active in this innovative spying field. Amnesty International suggests “advertisement-based infection methodologies are being actively developed and used by multiple mercenary spyware companies, and by specific governments who have built similar ADINT [advertising intelligence] infection systems.” That the digital advertising ecosystem has been subverted to hack the phones of unsuspecting citizens demands urgent industry action, which is as yet unforthcoming.
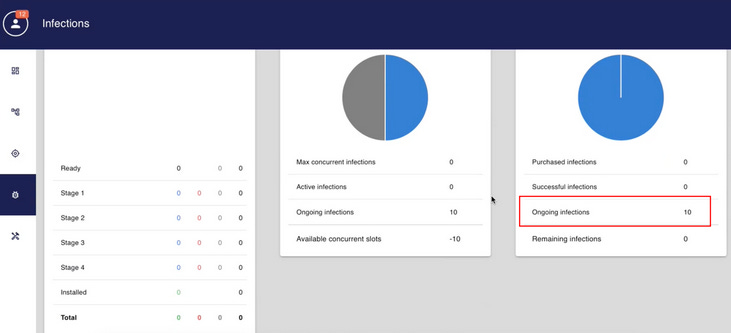
Just as disquietingly, a leaked Intellexa training video depicts how the Intellexa can “remotely access and monitor active customer Predator systems.” In effect, the firm is able to keep an eye on who its clients are spying on, and the precise private data they are extracting, in real-time. Recorded in mid-2023, the video begins with an instructor connecting directly to a deployed Predator system via TeamViewer, a commercial remote access software. Its contents suggest Intellexa can peruse at least 10 different customer systems simultaneously.
This capability is amply highlighted in the leaked video, when a staff member asks their trainer if they’re connecting to a testing environment. In response, they state a live “customer environment” is being accessed instead. The instructor then initiates a remote connection, showing Intellexa staffers can access highly sensitive information collected by customers, including photos, messages, IP addresses, smartphone operating systems and software versions, and other surveillance data gathered from Predator victims.
The video also appears to show “live” Predator infection attempts against real-life targets of Intellexa’s clients. Detailed information is shown from at least one infection attempt against an individual based in Kazakhstan, including the malicious link they unwittingly clicked that enabled their device’s infiltration. Elsewhere, domain names imitating legitimate Kazakhstani news websites, designed to trick users, are displayed. The country’s government is a confirmed Intellexa client, and local youth activists have previously been targeted by the notorious, similarly Israeli-incubated Pegasus spyware.
‘Business Opportunity’
The leaked video raises a number of grave concerns about Intellexa’s operations. For one, the shadowy, high-tech digital spying entity employed TeamViewer, a commercial software about which major security concerns have long-abounded, to access highly sensitive, invasive information on customer targets. This raises obvious questions about who else might be able to pry on this trove. Moreover, there is no indication Intellexa’s clients approved this access for training process, or the tutorial was conducted with even basic safeguards in place.
As such, the targets of Intellexa’s suite of spying resources not only face having their most sensitive secrets exposed to a hostile government without their knowledge or consent, but a foreign surveillance company in the process. The extent to which Intellexa is cognisant of how its technology is used by its clients is a core point of contention in the ongoing Greek legal case. Historically, mercenary spyware companies have firmly insisted they aren’t privy to data nefariously seized by their customers. Amnesty International states:
“The finding that Intellexa had potential visibility into active surveillance operations of their customers, including seeing technical information about the targets, raises new legal questions about Intellexa’s role in relation to the spyware and the company’s potential legal or criminal responsibility for unlawful surveillance operations carried out using their products.”
The latest disclosures about Intellexa have all the makings of a historic, international scandal, in the precise manner the use of Pegasus by state and corporate entities the world over has elicited international outcry, criminal investigations, and litigation lasting many years. However, the proliferation of ominous private spying tools, and their industrial scale abuse by paying customers, is no aberrant bug, but an intended upshot of the Zionist entity’s relentless crusade for cyberwarfare supremacy. In 2018, Israeli premier Benjamin Netanyahu boasted:
“Cybersecurity grows through cooperation, and cybersecurity as a business is tremendous...We spent an enormous amount on our military intelligence and Mossad and Shin Bet. An enormous amount. An enormous part of that is being diverted to cybersecurity...We think there is a tremendous business opportunity in the neverending quest of security.”
This investment manifests in almost every area of Israeli society. Numerous universities in Tel Aviv, with state support, hone new technologies and train future generations of cyber spies and digital warriors, who then join the Zionist Occupation Force’s ranks. Once their military service is complete, alumni frequently found companies at home and abroad offering the same monstrous services road-tested against Palestinians to private sector bodies and governments, without any oversight or guarantee these resources won’t be used for malevolent purposes.
The intelligence failures that enabled the success of Operation Al-Aqsa Flood in October 2023 did enormous damage to Israel’s credibility as a cybersecurity leader, while devastating its “Startup Nation” brand, with foreign investment in the entity’s tech industry collapsing precipitously. However, the fresh Intellexa revelations show certain elements of the sector remain in high demand, and pose an unseen threat to untold numbers of people globally. Should the firm fall into disrepute as a result, another surely waits in the wings to take its place.




Thanks for the excellent article.
Those in control do not want to lose control.
Israel uses dirty tricks, granted.
What does anyone propose to do about it? Screaming "No fair!" is not going to stop them.